Dynamic Application Security Testing
In this post, I talk about dynamic application security testing and why Netsparker is my weapon of choice.

... or how I learned to stop worrying and love Netsparker
Introduction and background
Before I continue with this post, let me be totally clear that there's no 'fanboy' relationship between me and my preferred DAST tooling provider. The relationship is one of trial, error and ultimate and ongoing success. In this post my aim is to replay that trip, talk about where I am now and what the future might look like.
Worry
If you read my earlier posts, you'll recall that we took a decision to buy in a tool that we could use to go and find all of the known web application vulnerabilities in our public facing software estate.
As we knew practically nothing about the security of our apps at the time, there was more than a little anxiety about what we might find. We had a combination of ancient / legacy / current production systems out there, as well as more modern stuff. Pressing 'Start Scan' felt easier said than done.
We installed Netsparker on a dedicated server, with a modest spec, which had no other workloads, as we didn't at the time know how it used compute power, RAM or how much storage it needed. More on that later on.
Early learnings
When I ran the first ever scan using Netsparker, it took ages (as far as I was concerned) and I didn't immediately understand why. Rather than write it off as a clunky application though, I went and looked at what it was actually doing. I was literally blown away.
Imagine hiring a team of hackists and asking them to carry out every method of SQL injection they know against a single website, using every vector they know. It might take that team days, if not weeks to find and then successfully exploit a vulnerability.
Netsparker does that automatically, over at most a few hours. It's also very cute, because it actually tests the vulnerability in a 'friendly' way before letting you know about it. It also provides you with an example of how it was able to successfully exploit the vulnerability, so you can go off and replicate it for yourself. Meanwhile your team of hackists are still manually crafting their dodgy attacks.
So, let's expand out from that particular vulnerability (albeit a killer) and bring in cross-site scripting, file inclusion, remote code execution, open redirection, cookie fails, shit headers, awful TLS and so on (it's a long list). It executes the same depth of testing for all of those problems too.
How long would it take that many people to test for all that stuff manually. I'll tell you - absolutely ages!
You get it. It does the work of a thousand testers in a fraction of the time it would take them.
What's your poison?
In other words, does it play with your particular web application technology choices?
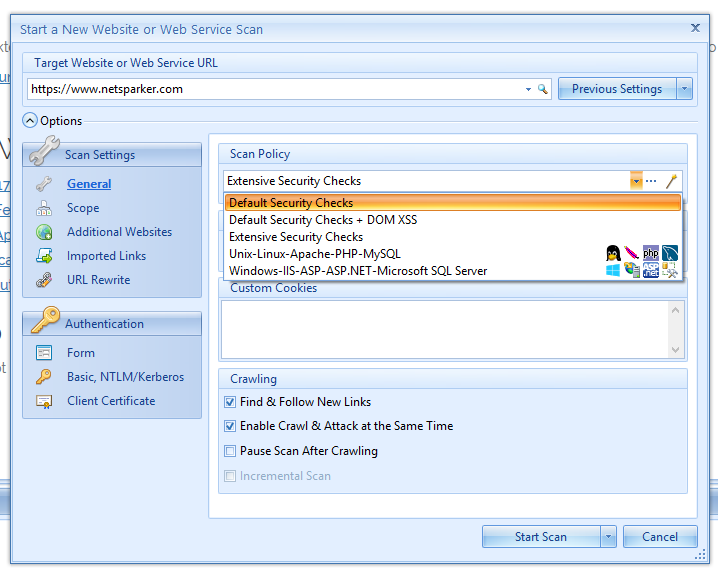
The answer is yes.
It gets ASP / .Net, Java, PHP, Ruby and Perl.
It gets IIS, Apache, Tomcat and NGINX.
It also gets MSSQL, MySQL, Oracle, PostgreSQL and the horrible MSAccess
Pretty much every enterprise level stack is covered, as well as the many open source frameworks and libraries, such as jQuery, Node and the like.
Aside from your choices of technology, some things are kind of independent of that, for example:
- Cookie security
- Transport security
- Well configured response headers
- Supporting HTTP verbs that might bite you on the arse
- Badly or not at all configured error pages
- Internal server errors that might disclose information useful to an attacker
- Disclosing stack tracing / view state that might allow an attacker to work out how your code works
The list goes on, but importantly Netsparker gets these things and hunts them out. While you eat your lunch.
From a web application security point of view, it covers all the bases, but it provides far more than that. It gives valuable insight into the problems that may exist where the application lives
Other notable bits
Netsparker contains tools in itself, for those still not quite convinced that automation is the absolute answer. For example, it has a tool to allow you to create HTTP requests and analyse the responses, a la Fiddler. It has a SQL injection tool that allows you to manually replicate or deep dive into a vulnerability it may have discovered, a la Havij.
You can run its 'Hawk' tool to detect out of band vulnerabilities and other things besides. This is the complete package, as far as I’m concerned.
It's telling me I have problems!
Well, that's Netsparker's job, but how does it go about telling you?
The UI is the start. I've used Troy Hunt's Hack Yourself First website to illustrate. He won't mind.
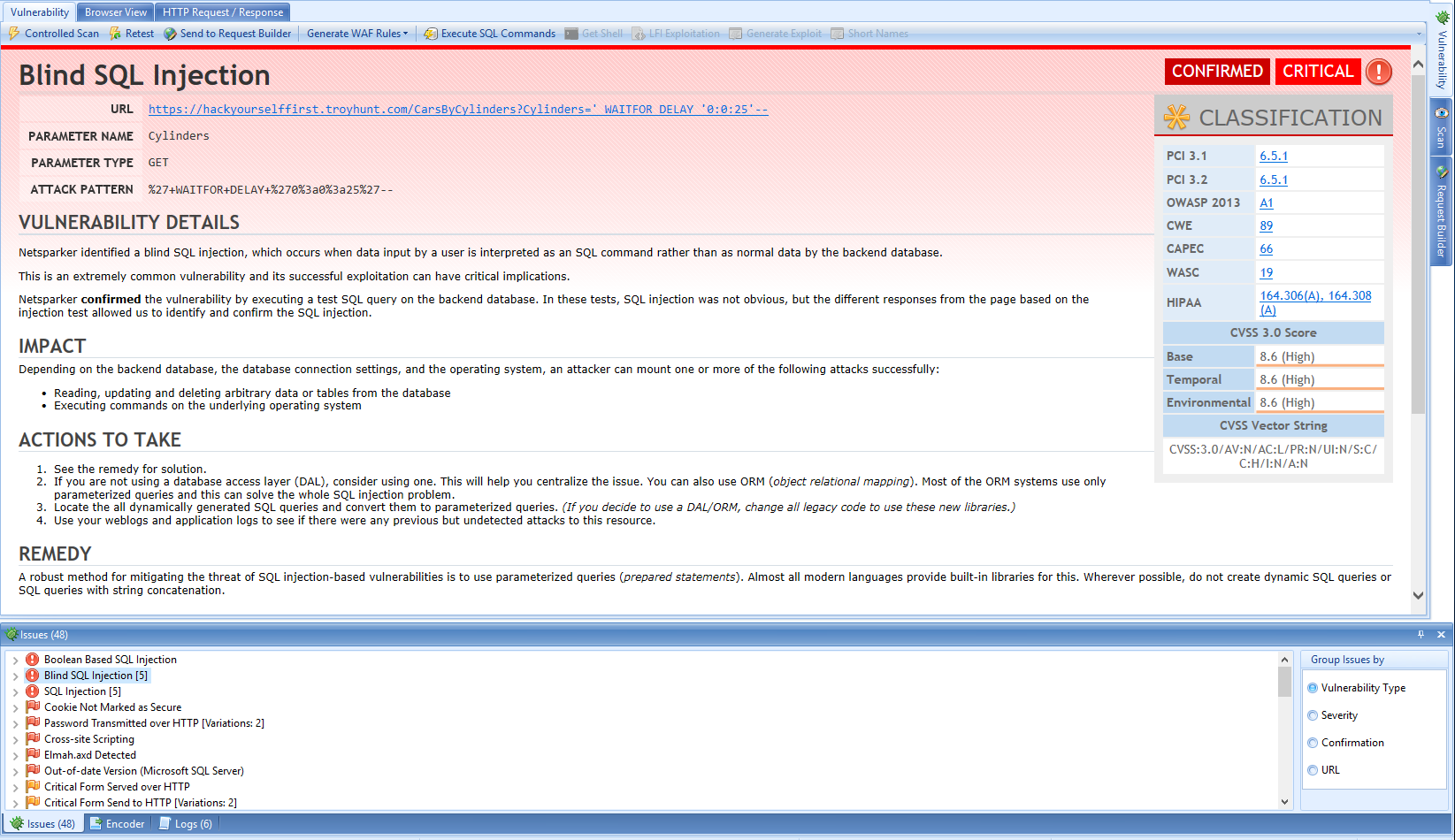
Take a look at this image. In the bottom pane, you're presented with a list of vulnerabilities that Netsparker has found, ordered by severity. In this example, they're pretty bad. That's deliberate, as this site has been stood up to demonstrate bad web application security practices.
In the top pane, you see the real meat of the problem; a detailed explanation of it, how it might cause you a problem, the proof of its existence and how to go about fixing it.
You also get the rather neat indicator of its severity in the context of known standards such as PCI-DSS, industry good practice such as OWASP and so on.
- Problem
- Context
- Severity
- Solution
That's a lot of output for a non-human.
Reporting
Right, Netsparker has discovered all these things. Now what?
Handily, it provides reporting in a wide variety of formats, aimed at a range of audiences:
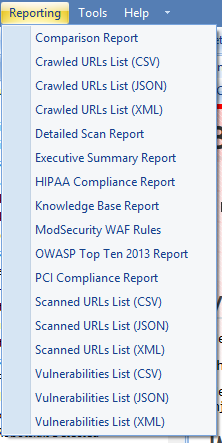
If I need to discuss a specific vulnerability with a developer, I opt for the 'Detailed Scan Report', as it contains the entire detail as described up above (problem, context, severity and solution). This helps, as I can confidently talk about why something is a problem, in terms a dev gets and also walk them through how to sort it out.
I use the 'OWASP Top Ten 2013 Report' to talk developer managers through the problems and place them into the context of the key known universal vulnerabilities, so that they can understand them and prioritise work effectively.
I use the 'PCI Compliance Report' to talk to higher level technology or business managers about the risks of not fixing problems in payment systems and present the possible consequences of that.
As I mentioned in a previous post, I do a lot of testing of third party, off the shelf software. The 'Vulnerabilities List (CSV)' export helps with that, as I can add my own narrative and recommendations.
There's something for every audience and it all helps inform decisions and ultimately leads to improvements.
What else?
Netsparker can create web application firewall (WAF) rules for you (if you use Mod_Security). That's pretty cool. It can construct work items or issues in your source control or project management platforms, such as GitHub, TFS or Jira.
We now have full automation of the scanning and porting of results into other systems, using a mixture of AWS, PowerShell and other technologies. I’m happy to discuss this in more detail with anyone interested.
Looking forward, we may very well make use of their SaaS offering, to lighten the load on our own resources and make use of the comprehensive inbuilt alerting functionality. It’s all on my to do list.
Netsparker as a company
That's pretty much the technology covered, but what are Netsparker like to do business with?
I'll summarise in the best way I can think of:
Friday, September 15th 2017.
11:41 - Issue discovered and reported
15:21 - Hotfix delivered
I was scanning a web application that our company is considering purchasing, when Netsparker suddenly threw an error and crashed. So, I raised a support ticket.
It was inside 15 minutes before an engineer contacted me to say he was looking into the problem and as you can see from the above mini-timeline, it was dealt with by mid-afternoon. You'll struggle to find that level of support in any software delivery cycle, let alone a commercial one.
I'm a small customer of Netsparker, relatively speaking, but that's really the whole essence of them as a company - it doesn't matter who you are. If you look at their marketing site, you'll quickly figure out that they look after Disney, NASA, Siemens, Sony (the list just goes on). They also look after Mike in the same way, the same response times and the same level of quality of service.
This is a professional operation, make no mistake. But it's also a human driven one, that cares about its customers, no matter who they are.
In summary
I recently posted a bunch of thoughts, views and whatnot about Netsparker on Twitter. I then collected and stuck them in one post:
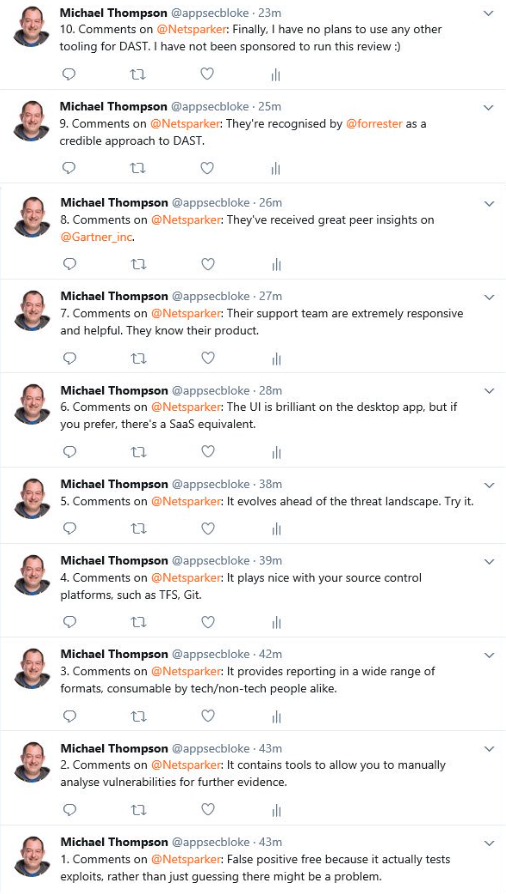
I stand by these views.
Netsparker is a superb product, which evolves with the web application threat landscape. Its people are fantastic, from leadership, through product development and support and business development.
My job would be incredibly difficult without it and the full picture of the security of our web applications would be a mystery.
Download a free trial, give it a go and you'll learn to stop worrying and love it.
Thanks for reading.
